Du kan ikke være for forsigtig, når det gælder din organisations online sikkerhed. Omfanget og sofistikeringen af cybersikkerhedstrusler stiger i hastig hastighed, hvor tre ud af fire amerikanske virksomheder risikerer et væsentligt cyberangreb (hændelser, der har en væsentlig indvirkning på en virksomheds finansielle stilling). Som et resultat ser mange virksomheder kritisk på deres nuværende praksis med hensyn til infosikkerhed.
En betydelig mængde personlige, økonomiske og fortrolige oplysninger opbevares trods alt på din virksomheds onlinekonti, og databrud resulterer ofte i tab af indtægter. For de fleste organisationer er der ét simpelt trin, der kan hjælpe med at forbedre dine medarbejderes cybersikkerhedsdisciplin på tværs af linjen: tofaktorgodkendelse (2FA), også kaldet multifaktorgodkendelse (MFA).

Tofaktorgodkendelse forklaret
Godkendelse er processen med at verificere en brugers identitet for at etablere adgang til et computersystem eller online-konto. Der er tre hovedfaktorer til godkendelse:
- En vidensfaktor (noget du kender, f.eks. et kodeord eller en pinkode).
- En besiddelsesfaktor (noget du har, f.eks. en mobilenhed eller et ID-kort).
- En iboende faktor (noget du er, f.eks. et fingeraftryk eller din stemme).
Der er også "lokalitetsfaktorer" og "tidsfaktorer", men disse er meget mindre almindelige. Tofaktorgodkendelse betyder simpelthen, at dit sikkerhedssystem bruger to af disse faktorer.
Med andre ord er tofaktorgodkendelse endnu et sikkerhedslag udover din adgangskode eller PIN-kode. Hvis du – efter at have logget ind med din adgangskode – nogensinde er blevet bedt om at indtaste en numerisk kode, der er sendt til dig på din mobile enhed for at bevise din identitet, er du allerede bekendt med 2FA.
At få en kode via tekst er imidlertid ikke den eneste metode til tofaktorgodkendelse. Der er en bred vifte af muligheder, herunder godkenderapps, push-meddelelser, softwaretokener, stemmebaseret godkendelse osv. I de fleste tilfælde er det ekstra sikkerhedslag sandsynligvis en SMS-kode.
Hvad er en godkenderapp?
Du er sandsynligvis bekendt med de fleste typer tofaktorgodkendelse, såsom sms'er, stemmebaserede meddelelser og push-meddelelser, men du er muligvis mindre bekendt med godkenderapps. Faktisk er de relativt enkle.
Så hvad er en godkenderapp? Kort fortalt er det en app på din mobiltelefon, der genererer digitale bekræftelseskoder, som kan bruges til at bekræfte din identitet, når du logger ind på et websted eller en applikation. Der er mange forskellige autentificeringsapps at vælge imellem, inklusive Google Authenticator App og Duo Mobile- som alle følger nogenlunde den samme procedure.
Godkenderapps anses generelt for at være en lidt mere sikker form for 2FA end at modtage en adgangskode til SMS-beskeder. Det skyldes, at SMS'er teknisk set ikke er noget, du har, men noget du får tilsendt.
Som sådan er der en lille chance for, at hackere kan narre din operatør til at portere dit mobiltelefonnummer til en anden enhed (en form for svindel kendt som "SIM-swap"). Forudsat at de allerede har din adgangskode, vil dette gøre det muligt for en hacker at få adgang til din konto. I kontrast udløber verifikationskoderne for godkenderapps meget hurtigt (normalt efter 20 eller 30 sekunder), og koden forbliver i appen.
Hvordan fungerer to-faktor-godkendelse?
Hvordan fungerer 2FA? Når du har konfigureret tofaktorgodkendelse på dit system – uanset om du bruger en godkenderapp, push-meddelelser eller SMS'er – er det relativt nemt at bruge. Her er en trinvis vejledning til selve 2FA-processen:
- Brugeren bliver bedt om at logge ind af hjemmesiden eller applikationen.
- Brugeren indtaster deres brugernavn og adgangskode, hvilket opfylder den første sikkerhedsfaktor.
- Når webstedet genkender brugeren, bliver denne bedt om at starte det næste trin i loginprocessen. Nu skal brugeren bevise, at de har noget som et ID-kort eller en smartphone, der opfylder den næste sikkerhedsfaktor, dvs. ”besiddelse”. I de fleste tilfælde får brugerne tilsendt en engangssikkerhedskode, som de kan bruge til at bekræfte deres identitet.
- Endelig indtaster brugeren sikkerhedsnøglen, og når webstedet har godkendt den, får de adgang.
Hvorfor bruge tofaktorgodkendelse?
Vigtigheden af at sikre din virksomheds filer og indhold kan ikke overvurderes. Globale cyberkriminalitetsskader anslås at nå op på omkring 15,63 billioner dollars årligt i 2029. Omkostningerne forbundet med cyberkriminalitet omfatter ødelæggelse/misbrug af data, stjålne penge, afbrydelser efter angreb, tyveri af intellektuel ejendom og tabt produktivitet.
Men du der er også potentielle udgifter forbundet med gendannelse af hackede data/systemer, retsmedicinsk undersøgelse og omdømmeskader.
Da trusler bliver mere og mere sofistikerede, og resten af verden implementerer tofaktorgodkendelse som standard, risikerer virksomheder, der ikke gør dette, at de er sårbare over for destruktive hackere. Det er ligesom ikke at bruge sikkerhedssele, fordi bilen har airbags. Teknisk set er du beskyttet, men ikke helt så beskyttet som du kunne være.
Hvorfor du ikke skal stole på "stærke" adgangskoder
Når det gælder onlinesikkerhed er den mest almindelige godkendelsesfaktor kombinationen af brugernavn/adgangskode. Dette betyder, at de fleste systemer kun bruger ettrinsgodkendelse. Selvom adgangskoder har været standard til infosikkerhedsstandard i årtier, er der flere grunde til, at det endelig kan være på tide at gå helt væk fra adgangskoder.
1. Mennesker har tendens til at have dårlige minder
Det er desværre givet. Plus i mange tilfælde er de adgangskoder, vi vælger, komisk nemme at gætte: "adgangskode", "12345", "qwerty" og så videre.
2. Folk har flere onlinekonti, end de havde, da adgangskoder først blev introduceret
Det betyder, at der ofte simpelthen er for mange adgangskoder til at huske. Dette kan føre til "adgangskodegenbrug", hvilket er når den samme adgangskode bruges til flere konti, hvilket gør det nemmere for hackere at få adgang.
3. Nogle websteder bruger sikkerhedsspørgsmål
For eksempel "Hvad er din mors pigenavn?" som en slags anden faktor. Med en sådan overflod af personlige oplysninger tilgængelige på nettet er hackere ofte i stand til at gætte svarene på disse relativt grundlæggende spørgsmål.
Det er vigtigt at bemærke, at sikkerhedsspørgsmål blot er en sekundær vidensfaktor, og denne praksis er ikke "ægte" 2FA. Du sikkerhedskopierer i bund og grund en adgangskode med en anden adgangskode.
Konklusion: Adgangskoder er den laveste form for sikkerhed, hvorfor tofaktorgodkendelse i stigende grad bliver den grundlæggende sikkerhedsstandard for virksomheder.
Mere end tofaktorgodkendelse
Fordelene forbundet med to-faktor autentificering er betydelige. Men 2FA er ikke den endelige destination for informationssikkerhed. Langt fra.
Tofaktorgodkendelse er trods alt ikke idiotsikret. Hvis en hacker ønsker at få adgang til dine computersystemer, kan en fysisk søgning i dine lokaler resultere i fund af et medarbejder-id eller en kasseret lagerenhed, der indeholder adgangskoder.
Desuden kan hackere opfange tekstbeskeder via phishing-e-mails, hvilket muligvis giver dem mulighed for at omgå den anden godkendelsesfaktor. I sidste ende er 2FA kun så stærk som det svageste element i sikkerhedsprocessen.
Alternativer til to-faktor autentificering
Så hvad kan man ellers gøre? 2FA er simpelthen en delmængde af et meget større koncept: multifaktorgodkendelse (MFA).
I teorien kan du have trefaktorgodkendelse, firefaktorgodkendelse, femfaktorgodkendelse og så videre i det uendelige. Mens almindelige brugere sandsynligvis aldrig kommer til at bruge noget ud over tofaktorgodkendelse, kan folk, der arbejder i miljøer med høj sikkerhed, være forpligtet til at bruge noget som trefaktorgodkendelse (3FA), som typisk involverer brugen af en egenfaktor, såsom et fingeraftryk eller en iris-scanning.
Sådan får du tofaktorgodkendelse (2FA) med Dropbox
Det er klart, at aktivering af tofaktorgodkendelse (2FA) kan have alvorlige fordele for din virksomhed, men processen med at implementere 2FA på tværs af hele din virksomhed kan være lidt skræmmende. Heldigvis behøver det ikke at være en alt for stor udfordring.
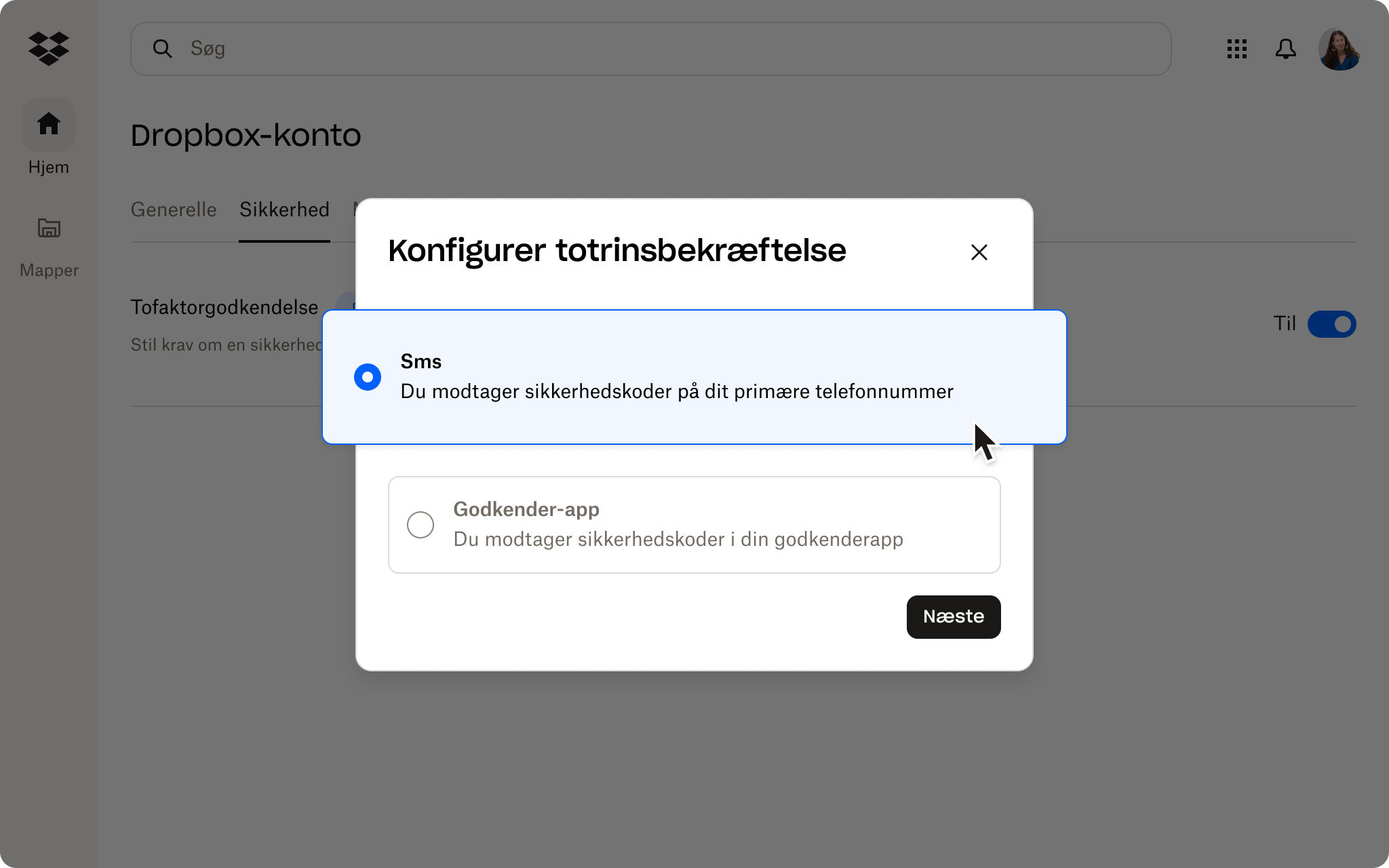
Dropbox tilbyder tofaktorgodkendelse og giver administratorer mulighed for at kræve det for teamet i administratorkonsollen. Hvis du er en eksisterende Dropbox-bruger, kan du opsætte 2FA her– uanset om du er administrator, teammedlem eller individuel bruger. Administratorer kan også kræve, at deres team opsætter 2FA direkte fra administratorkonsollen.
Hvis du konfigurerer 2FA, kræver Dropbox, at du angiver en anden form for godkendelse (f.eks. en sekscifret kode via sms eller en godkendelsesapp eller en sikkerhedsnøgle), når du logger ind på en konto eller tilknytter en ny tablet, computer eller telefon.
Derudover tilbyder Dropbox en række funktioner til adgangskodebeskyttelse, der kan hjælpe dig med at sikre og kontrollere din virksomheds følsomme oplysninger, mens du også kan angive udløbsdatoer for delte links og adgangskodebeskyttelse af dine PDF-filer og mapper.
Der er andre cybersikkerhedsforanstaltninger, som du kan implementere med Dropbox for at hjælpe med at beskytte dine filer endnu mere effektivt. Cloud-databeskyttelse er vores topprioritet, og cloud-sikkerhed er et ideelt supplement til to-faktor-autentificering. Med flere lag af beskyttelse på tværs af en distribueret cloud-infrastruktur kan du sikre, at alle dine onlinefiler ydes det samme niveau af beskyttelse. Derudover kan krypteret cloud-lagring i virksomhedskvalitet bruges til at overholde de fleste globale regulatoriske standarder.
Hold dine data sikre, og drag fordel af 2FA med Dropbox
At stole på en enkelt adgangskode som kun beskyttelse af dine filer og data gør dig sårbar over for trusler, der kan forhindres. Med 2FA gør du det langt sværere for dårlige skuespillere at få adgang til dit indhold.
Uanset om du allerede er en Dropbox-bruger på udkig efter lidt ekstra ro i sindet, eller du har brug for en cloud storage-løsning med flere lag af beskyttelse – Dropbox har dig dækket.
Tilmeld dig en konto for at begynde at drage fordel af to-faktor-godkendelse i dag.