In today's digital world, ensuring the protection of personal data is of utmost importance as our dependence on technology grows and our production of confidential data increases. In this piece, we'll explore the idea of data security, examining its importance and the different types of data security.

What is data security?
Put simply, data security is the process of safeguarding and protecting digital information from vulnerabilities such as unauthorized access, insider threats, corruption, or theft.
It encompasses a comprehensive range of data loss prevention measures, including:
- The on-premises, physical security of hardware and devices
- User permissions and data access controls
- Security policies and procedures to protect an organization’s data
What’s the difference between data security and data privacy?
Data security and data privacy are often used interchangeably. However, they are slightly different:
- Data security—the measures taken to protect data from malicious activity
- Data privacy—the strategic decisions over who can access sensitive or confidential information
For instance, data security measures might involve encrypting data during transmission, to prevent hackers and unauthorized users from accessing it. Data privacy regulations and policies might specify who is authorized to view certain files, such as health information.
.png?id=e4b375d0-a045-468a-b4b2-c32facc0786c&output_type=png)
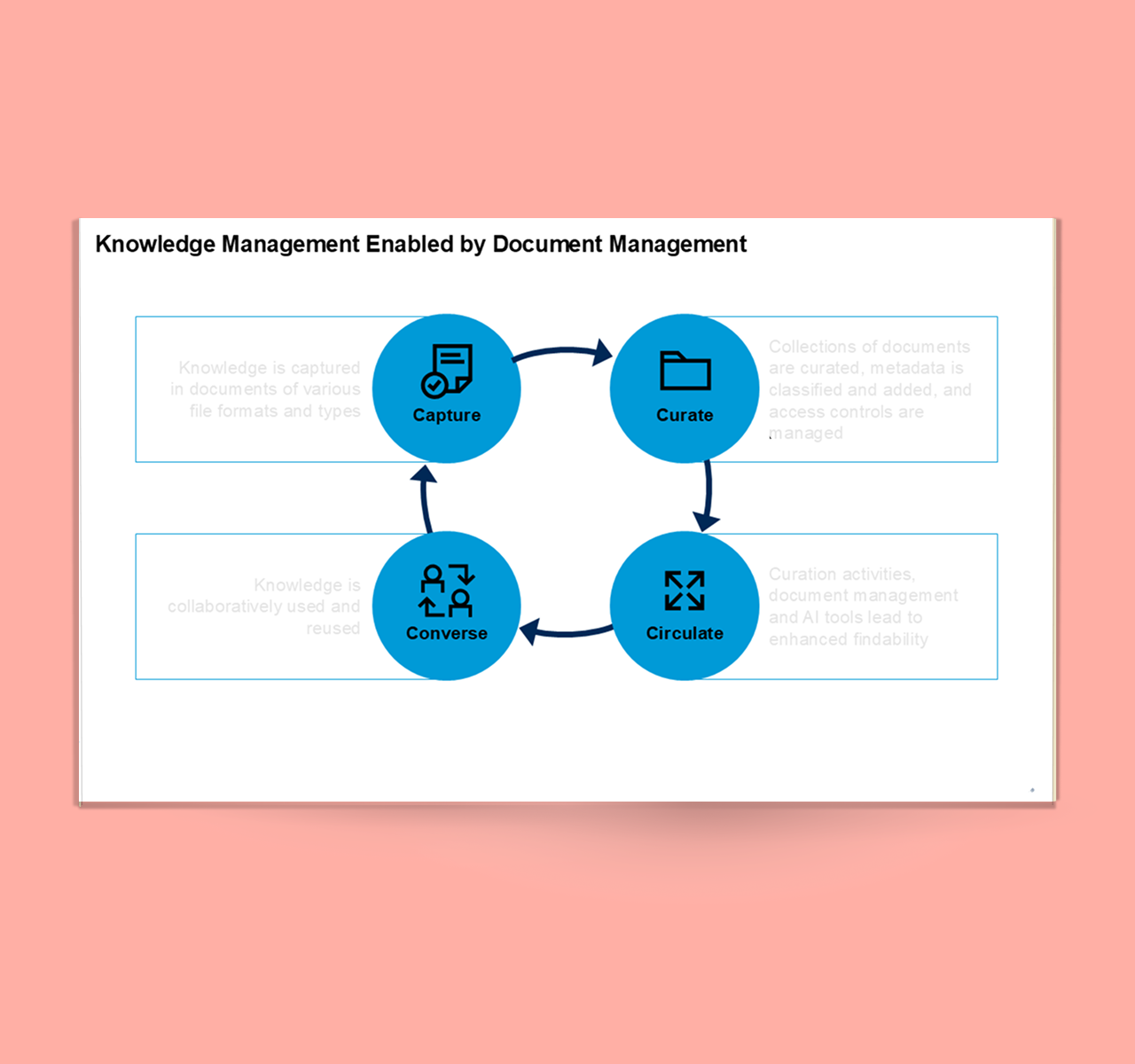
Different types of data security
There are several key types of data security measures that organizations can use to protect their information:
Encryption
Encryption involves using algorithms to “scramble” data while it’s being transferred from one device to another, whether it’s over the internet, through a local network, or between two endpoints. This ensures that, even if the data is intercepted during transmission, only authorized users with the correct decryption “key” can unscramble it.
Dropbox offers end-to-end encryption for users’ cloud data, ensuring your files are encrypted and decrypted on approved devices only.
Data erasure
Data erasure refers to the permanent deletion of a data set when it reaches the end of its lifecycle and is no longer needed. It’s achieved through methods such as overwriting the existing data with random patterns or zeros multiple times. This makes it virtually impossible for anyone to reconstruct the original information and is a more effective method than standard data wiping.
Data erasure is essential for compliance with various data protection regulations, such as the General Data Protection Regulation (GDPR) in Europe or the Health Insurance Portability and Accountability Act (HIPAA) in the United States. These regulations mandate that organizations take appropriate measures to protect sensitive information and ensure it can’t be accessed once it’s no longer needed. Failure to comply with these regulations can result in severe penalties and damage to an organization's reputation.
Data masking
Data masking is a form of encryption that obscures and replaces specific letters or numbers in the data code.
This process involves altering the original data in such a way that it remains usable for various purposes, such as testing, analysis, or training, while ensuring that the actual sensitive information is not exposed. Only someone with the code to decrypt or replace the masked characters can unlock the data.
For example, in a dataset containing personal identification numbers (PINs), a masked version might replace the actual digits with asterisks or random numbers, making the original information unreadable. Masking is essential in environments where data needs to be shared or accessed by individuals who don’t have the necessary permissions to view the original data.
Data resiliency
Data resiliency focuses on ensuring the availability and integrity of data in the face of various threats and challenges. It involves creating data backups or copies so that it can be easily recovered in the event of a data security incident, such as if it’s stolen, damaged, or simply lost due to human error. This provides a crucial safety net that allows you to recover important information when unforeseen circumstances arise.
But data resiliency isn’t just about backups—it also involves regular audits and testing of these backups to validate that they’re functional and up to date. By doing so, you can identify any potential weaknesses in your data security solutions and make necessary adjustments.
Why is data security important?
In today’s digital landscape, almost everything we do in work is digital. As a result, we generate an immense amount of data every day—data that’s increasingly at risk of cybersecurity threats such as malware, ransomware, phishing, and more. Traditional data protection methods that were effective for physical files and folders are no match for modern cybercriminals.
With the rise of remote and hybrid work, the safety and integrity of a company’s sensitive data and intellectual property has become even more important. Research conducted by IBM and Ponemon Institute revealed that breached data stored in public clouds incurred an average cost of USD 5.17 million.
Robust, straightforward data security with Dropbox
Implementing a comprehensive data security strategy is essential for protecting sensitive information against cyberattacks, data breaches, and unauthorized access. Cost-effective, secure, and user-friendly cloud environments like Dropbox enable you to safeguard your files, prevent devastating data loss events, and gain a competitive edge.
Advanced encryption from Dropbox empowers HR, Finance, and Marketing teams to securely manage sensitive data and meet both internal security policies and external compliance standards, including GDPR, HIPAA, and the California Consumer Privacy Act (CCPA).
Advanced key management allows teams to set up a unique encryption key as an added layer of security, ensuring that only members of their organization can access Dropbox files. End-to-end data encryption ensures that only users invited to an encrypted folder can access the files stored within it.
The Dropbox admin console provides comprehensive control over data security at an organizational level, encompassing all files stored in your team’s Dropbox account. This includes team folder management, an external sharing report and page, data classification tools for sensitive files and folders, and more.
These features ensure that no one—including Dropbox—can gain access to your files.